There has been a worrying increase in assaults and hacks targeting crypto during the past year. There have been far too many for anyone to keep count; this is a pressing problem.
Happily, when an exploit is discovered, protocols may improve their preparedness by reviewing code, monitoring network behaviour, and establishing defined attack response strategies. If the industry learns from this and adopts these safeguards, we may never see another year like this again.
A Series of Exploits and Attacks
Chainalysis predicts that the amount of money stolen by crypto hacks and exploits in 2022 will reach an all-time high. At the last check, around $3 billion was lost.
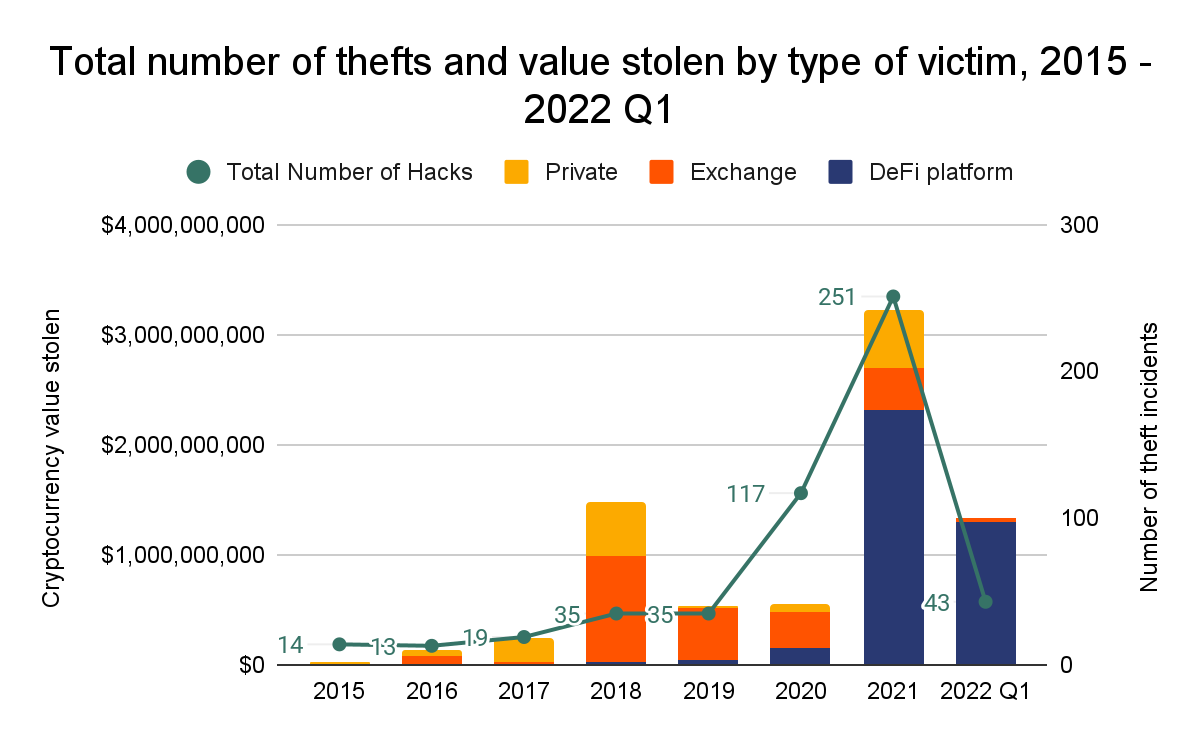
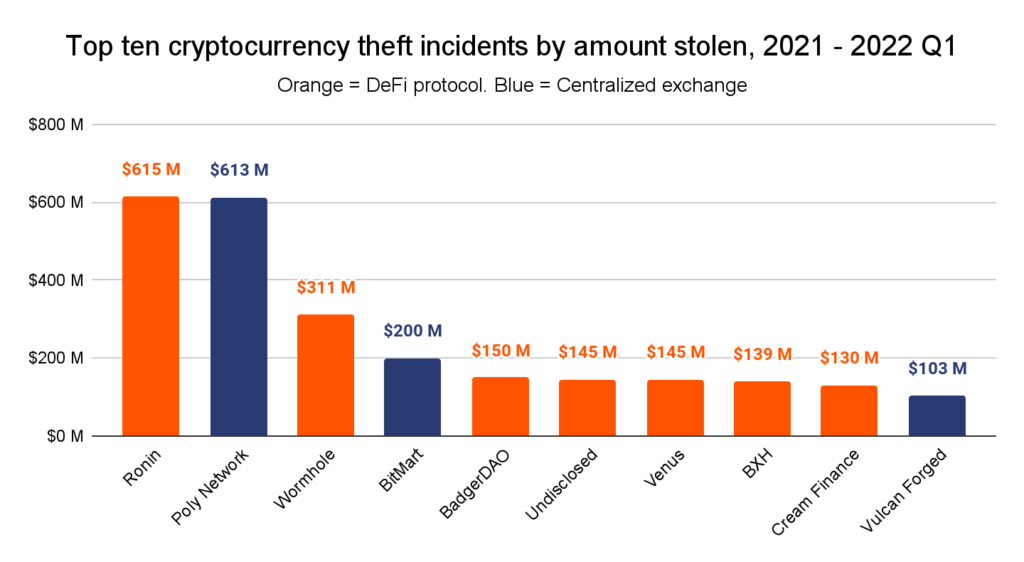
The hack of Ronin stands out as an example. In March, Lazarus Group, a group with ties to North Korea, stole $620 million worth of ether and USDC from the Ronin Network, a sidechain created for the massively popular Web3 game Axie Infinity.
The most unexpected part was that it took almost a week to find out about this attack. About $30 million has been recovered, and Binance has frozen another $5.8 million, but the rest is still in the hands of the hackers.
Furthermore, the February Wormhole bridge attack cost has yet to be recouped. Not the first, but the most significant attack on the bridge that links Ethereum, Solana, Avalanche, and other blockchain networks. Someone managed to create 120,000 wrapped ether (wETH) without putting up any collateral. They turned that free wETH into ETH and SOL, earning themselves $320 million.
This is only the beginning of an endless list. Nomad Bridge lost one hundred and 90 million dollars. $160 million was stolen from the decentralised finance (DeFi) network Wintermute and a Binance BNB Network bridge was used to suffer a $100 million loss. The security of bitcoin services must be improved to prevent hacking and other vulnerabilities.
Where to Go From Here
Fortunately, things can change for the better and won’t always be this bad. If crypto platforms and protocols are ready to strengthen their defensive measures, we will witness fewer assaults in 2023 and beyond, or at least reduce their impact. This can take many forms but always includes more thorough monitoring and faster, more effective responses when an incident occurs.
Trusted, independent parties should thoroughly examine all smart contract codes as the first protection strategy. Results of these audits should be made public for full disclosure of any issues and subsequent solutions.
However, as we have seen with the many DeFi platforms hacked, a single security assessment isn’t sufficient. Instead, fresh audits should be conducted every time the code is modified. So doing will guarantee that no unforeseen problems arise. Teams need to take a more security-centric approach while developing and releasing smart contracts since even a seemingly innocuous update to the code might have far-reaching consequences.
There should be fewer crypto-related exploits if audits were sufficient. Deploying code in a way that allows teams to mitigate against potential risk vectors is necessary even if the code has been adequately tested and audited. Customers can feel confident in the safety of their funds with the status of privileged accounts and the broader interrelationships between system components and the blockchain’s state.
Large or many transactions sent to the same address in a short period are often the first indicator of an attack. Capturing these incidents as they occur may keep teams abreast of developing dangers. Also, it paves the way for the automation of these safeguards, which would significantly reduce or do away with the need for human intervention.
Finally, monitoring operations and security won’t do much good without a reaction system. When a team has meticulously mapped the attack vectors of their systems, they may prepare for a security event in advance. To this end, conducting smoke tests and meticulously planning for a response is crucial. Damage can be stopped and reversed in hours or minutes rather than days or weeks.
Even if funds are lost, it’s essential to act quickly to stop it from happening again. This strategy may help restore faith in a protocol’s developers, even if their system has been demonstrated to be vulnerable.
Since a security-first mindset becomes the norm, it will discourage attackers from even trying to breach systems in the first place, as they know their efforts will be futile. Community-driven security monitoring projects strengthen the safety of the blockchain since they are incentivized and made transparent to all users.
Although there is no “one size fits all” solution, it is clear that regular audits, operational security and operational monitoring of networks, and automated incident notification and response mechanism would all be beneficial to any protocol. Such steps, done by pioneers in the Web3 ecosystem like Compound Finance and Matter Labs, have proven vital. If other teams adopt these safeguards, 2022 could be the last time the crypto space suffers a series of severe exploits and attacks.













