Crypto hardware wallet provider Ledger recently clarified the functionality of its firmware following the deletion of a controversial tweet on May 17. The tweet, supposedly written by a customer support agent, claimed that Ledger could develop firmware capable of extracting users’ private keys.
[1/3] You may have seen a tweet from our Ledger Support account being shared regarding Ledger firmware updates.
Unfortunately, in our attempt to clarify how Ledger and all wallets work with the firmware, a customer support agent posted a tweet with confusing wording. https://t.co/cL6UrBzxWr
— Ledger Support (@Ledger_Support) May 18, 2023
Charles Guillemet, the chief technology officer of Ledger, took to Twitter to provide clarification. He explained that the wallet’s operating system (OS) requires user consent whenever the OS interacts with a private key. The OS cannot copy the device’s private key without the user’s approval. However, Guillemet also noted that using a Ledger wallet necessitates placing a certain level of trust in the system.
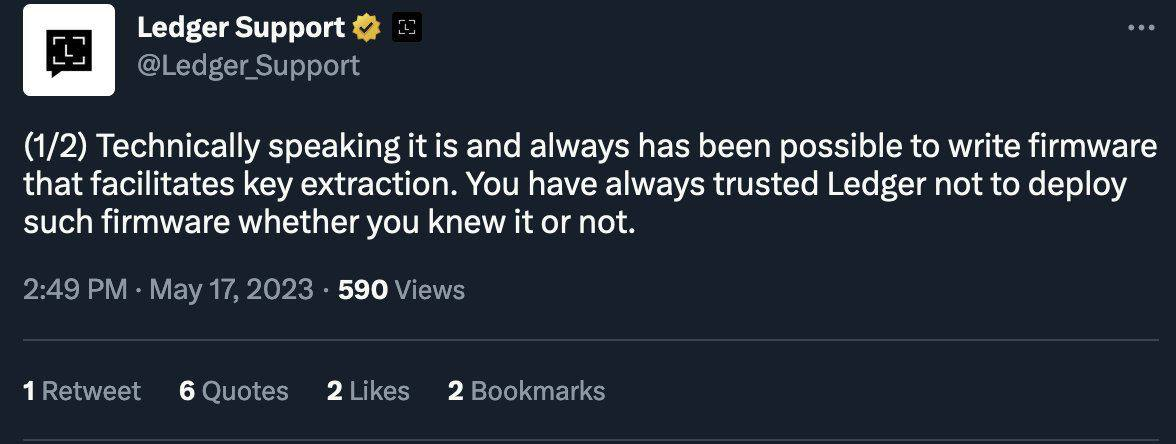
The original deleted tweet from Ledger’s customer service stated that it had always been possible to create firmware facilitating key extraction, but Ledger had never deployed such firmware. This tweet caused a significant controversy on Twitter, with many users accusing Ledger of misrepresenting the security of its wallets. Critics pointed to a supposed Ledger post stating that a firmware update couldn’t extract private keys from the Secure Element, which contradicted the deleted tweet.
Although the deleted tweet sparked the controversy, it began on May 16 when Ledger introduced the “Ledger Recover” service, enabling users to back up their recovery phrase by splitting it into three shards and storing them with different data custody services. The deleted tweet was a response to the release of this new feature.
Guillemet’s recent Twitter thread explained that the wallet’s firmware and OS operate as an open platform, allowing anyone to develop their app and load it onto the device. However, Ledger’s team evaluates and approves apps before they can be used with the Ledger Manager software to ensure they are not malicious and free of security flaws
Nov 2022: A firmware update cannot extract the private keys from the Secure Element — Ledger
May 2023: Technically speaking it is and always has been possible to write firmware that facilitates key extraction — Ledger@Ledger, do you now understand the problem? pic.twitter.com/czG53SuCOu
— olimpio (@OlimpioCrypto) May 17, 2023
Ledger asserts that even after an app is approved, the OS prevents it from using private keys associated with networks it is not designed for. For instance, a Bitcoin app cannot use the device’s Ethereum private keys, and vice versa. Additionally, Ledger states that every time an app employs a private key, user consent is required through the OS. Consequently, third-party apps installed on Ledger should not be able to use a user’s private key without explicit permission.
Guillemet also acknowledged that this system is part of the current OS, which could be modified if Ledger were to act dishonestly or if an attacker gained control over the company’s computers. However, he dismissed this concern, stating that a certain level of trust is necessary when using a wallet, and users would be doomed if they assumed their wallet provider was the attacker. The only way to entirely protect against a dishonest wallet developer is to build an entire computer, compiler, wallet stack, node, and synchroniser, which he described as a lifelong endeavour.
Rival hardware wallet provider GridPlus has offered to open-source its firmware to attract Ledger users. Conversely, Guillemet argued that open-sourcing firmware wouldn’t safeguard against a dishonest wallet provider since users would have no means of verifying whether the published code was genuinely running on the device.














